How To: Keep Data-Thieving USB Accessories from Connecting to Your iPhone in iOS 11.4.1 & Higher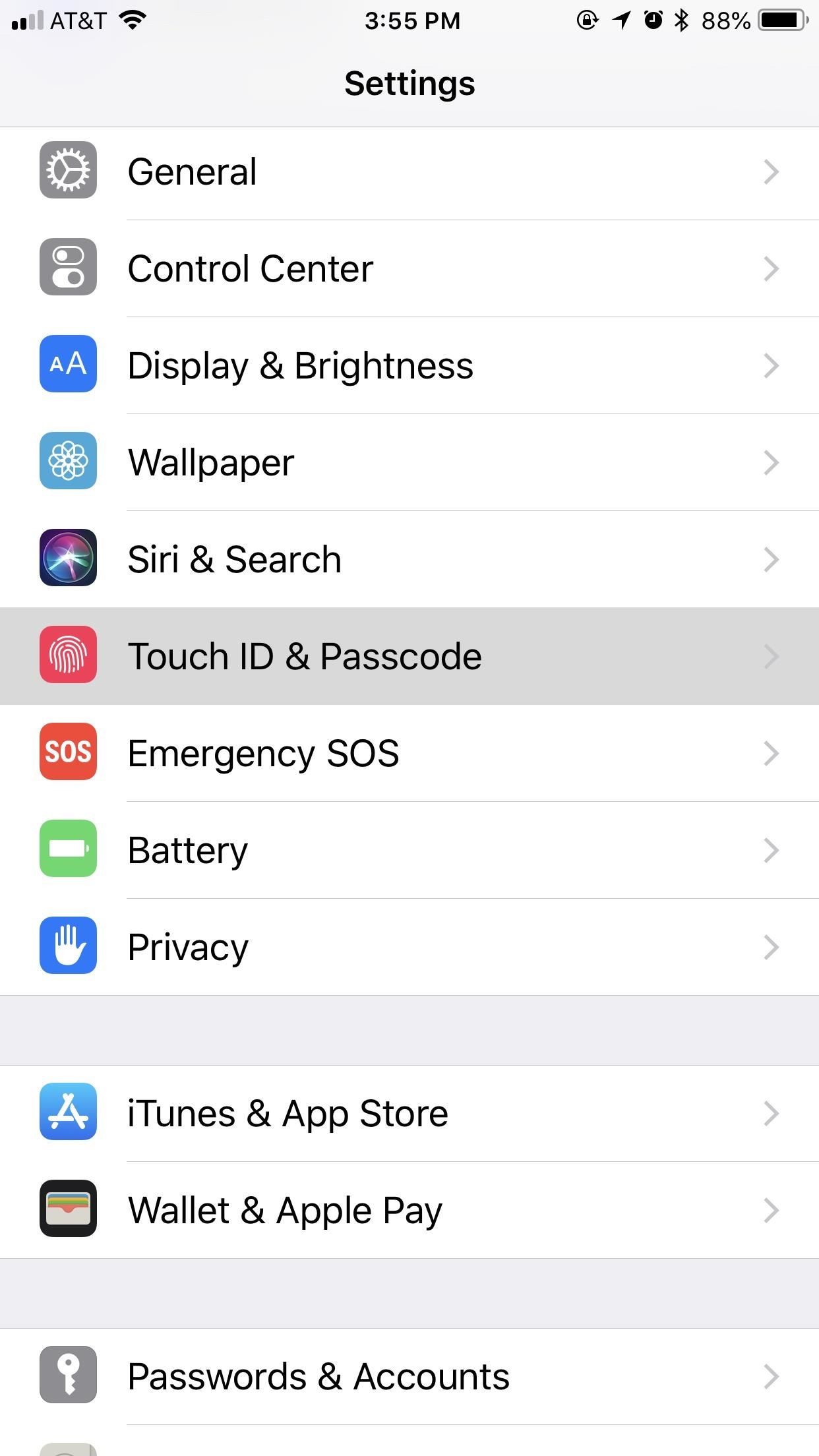
While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.This security feature initially debuted in the iOS 11.3 beta as "USB Restricted Mode," but didn't find its way to an official release until iOS 11.4. Previously, it would take seven days after last unlocking your iPhone for it to lock out all USB accessories, rendering brute-force tools such as GrayKey and Cellebrite utterly useless.Apple improved this feature in the iOS 12 beta first, but also in iOS 11.4.1, slashing the time it takes to keep those accessories at bay, a move that will please customers while likely frustrating law enforcement officials and maybe even hackers and thieves. Instead of seven days, USB Restricted Mode only takes one hour to kick in after locking your iPhone.Don't Miss: How to Create a Strong (Or Stronger) Passcode for Your iPhone This feature is enabled by default. To verify it's working, open up the Settings app, then enter your "Touch ID & Passcode" or "Face ID & Passcode" settings. There, you'll see a "USB Accessories" toggle under Allow Access When Locked, which should be off. If it's on for some reason, turn it back off to keep your iPhone secure. Don't Miss: Disable the 'Unlock iPhone to Use Accessories' Notification in iOS As mentioned above, this security feature doesn't work as soon as you lock your iPhone. It takes one hour after you last lock the iPhone for the setting to kick in. Once it does, your iPhone's Lightning port becomes nothing more than a place to charge your iPhone. However, this only applies to charge-only cables, like plugging into a wall outlet — not a computer.Any activity attempted through USB when protected will prove fruitless — even iTunes syncing on trusted computers — until your iPhone is unlocked via Face ID, Touch ID, or your passcode. You will get a "USB Accessory" notification saying to "Unlock iPhone to use accessories." Charging will also be disabled when this warning appears. Image by Justin Meyers/Gadget Hacks Once you've granted access to the USB accessory, your device will remain connected even after an hour; It won't quit while you're using it, even if it hasn't been unlocked within an hour. This means you can continue to do things such as view or play your Music collection in iTunes on your computer. Once you disconnect, the timer starts again from zero, and one hour later, if you try to reconnect that device, you'll need to unlock your iPhone again.Headphones and power-only accessories, such as the 5-watt USB power adapter that comes with your iPhone, should still work without unlocking first after the countdown. It's just anything it detects that is trying to transfer data to or from your iPhone that will be blocked.Charge It Faster: 30-Watt USB-C Power Adapter for iPhones on AmazonAlso worth noting, in the time before your iPhone automatically restricts data access on the Lightning port, you're just as vulnerable as you are without the setting. It's unlikely that unlocking services by Cellebrite, Grayshift, and other security firms that are employed by law enforcement officials will be able to hack a passcode in that hour time limit, though they may find a workaround.If you disable the "USB Accessories" setting (i.e., toggle it on), your iPhone will be susceptible to data transfers by USB accessories even after one hour. If your iPhone is stolen or otherwise taken from your possession, your passcode and biometrics might not be enough to protect your data. It's not yet known if USB accessories will be disabled after seven days without an unlock like it was back in iOS 11.4.Don't Miss: 50+ Cool New iOS 12 Features You Didn't Know AboutFollow Gadget Hacks on Facebook, Twitter, YouTube, and Flipboard Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image and screenshots by Jake Peterson/Gadget Hacks
Laser Beam Shows are considerably the most popular type of laser show that can be created. And the more professional the nature of the laser show taking place (for example a large festival, concert, tour, or theatrical event) the more detailed the laser beam effects need to be, to ensure they match the theme of the eve
HOW TO - Build a laser effects show | Make:
How to Send Files to a Cell/Mobile Phone Using Bluetooth
How to Use Your New Terabyte of Free Flickr Storage for More
If you want to read these steps in more detail, read our dedicated article on How to Unlock Samsung Galaxy S10e Bootloader. HOW TO: Root Galaxy S10e on Official Firmware. Here are all the steps you would need to root Galaxy S10e with Android 9.0 Pie firmware through Magisk utility and TWRP custom recovery. Just To Remember:
Unlock Bootloader, Root and Install TWRP on Verizon Galaxy Note 4
Visit
Are you tired of all of those applications bombarding you on Facebook?Spamming you all the time, never stopping? Are they just annoying? Well, this video tutorial will show you how to remove unwanted, spammy, or otherwise annoying apps on Facebook.
3 Ways to Remove Unwanted Apps that Won't Delete on Mac
Instruments Music Lessons & Resources Lessons Improvisation Pieces Playalong Jam tracks Licks & Riffs Chord Charts Tuners,Charts & Resources Free Sheet Music Categories Classical Pop & Rock Jazz Traditional Film & TV by Country by Decade Wedding Christmas Funeral Childrens Christian New Music
Free Sheet Music Downloads - Find Thousands
Create rules to filter your emails - Gmail Help
Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.
Hack Multiple Android Devices — Pioneer Update
pioneeravic.com/hack-multiple-android-devices
If you get connected to an answering service chances are something is wrong with the company. Build Your Own Media-Altering Newstweek Device How To:Glympse GPS tracking app is definitely the easiest as well as the most basic way of sharing your geographical location with someone. How Can I Spy On Other Android Phone
How to Use a Newstweek to change the news read by others on a
A mechanically powered flashlight is a flashlight that is powered by electricity generated by the muscle power of the user, so it does not need replacement of batteries, or recharging from an electrical source. There are several types which use different operating mechanisms.
L.L.Bean Flashlights | Premium Quality, Built To Last
AD
0 comments:
Post a Comment